Elevate Your Digital Presence
Explore tips and strategies to enhance your online engagement.
Data Transfer: The Great Digital Tug-of-War
Discover the thrilling battle of data transfer! Uncover secrets, tips, and strategies in the ultimate digital tug-of-war. Click to learn more!
Understanding Data Transfer: Key Concepts and Challenges
Understanding data transfer is essential in today's digital landscape, where the movement of information plays a crucial role in numerous applications. Data transfer refers to the process of transmitting data between devices or networks, which can happen through various protocols and methods. Key concepts associated with data transfer include bandwidth, latency, and throughput. Bandwidth is the maximum rate of data transfer across a network, latency is the time it takes for data to travel from the source to the destination, while throughput measures the actual amount of data sent successfully over a given period. Understanding these elements enables businesses and individuals to optimize their data transfer systems and improve overall efficiency.
Despite its importance, data transfer comes with several challenges that can impact performance and reliability. Some common challenges include network congestion, security concerns, and compatibility issues between different devices and protocols. Network congestion occurs when too many devices attempt to transmit data simultaneously, leading to delays and packet loss. Security is another significant concern, as sensitive information can be intercepted during the data transfer process. Lastly, ensuring compatibility between diverse systems can be cumbersome, requiring the use of appropriate standards and protocols to facilitate seamless communication. Addressing these challenges is crucial for any organization aiming to improve its data transfer capabilities.
Counter-Strike is a popular first-person shooter game that has captivated gamers around the world. The game emphasizes teamwork and strategy, where players are divided into two teams: terrorists and counter-terrorists. As players navigate various maps, they can gather resources, plan strategies, and execute tactics to outsmart their opponents. For those looking to enhance their gaming setup, check out the Top 10 usb c hubs for macbook to improve connectivity and performance.
Data Transfer Protocols Explained: A Guide for Beginners
Data transfer protocols are essential frameworks that govern how data is transmitted over networks. These protocols ensure the reliable exchange of data between devices, applications, and services. For beginners, understanding these protocols is crucial as they play a key role in various applications, from web browsing to email communication. Some of the most common protocols include HTTP (Hypertext Transfer Protocol), which is used for transferring web pages, and FTP (File Transfer Protocol), used for transferring files between computers. Familiarizing yourself with these protocols can greatly enhance your knowledge of how the internet functions.
There are several different types of data transfer protocols, each serving unique purposes in the networking landscape. Among the most commonly used protocols are:
- TCP (Transmission Control Protocol) - ensures reliable data transmission
- UDP (User Datagram Protocol) - allows faster, but less reliable, data transfer
- SMTP (Simple Mail Transfer Protocol) - used for sending emails
- IMAP (Internet Message Access Protocol) - used for retrieving emails
By exploring these protocols and their functions, you'll gain a deeper appreciation for the technology that underpins modern communication.
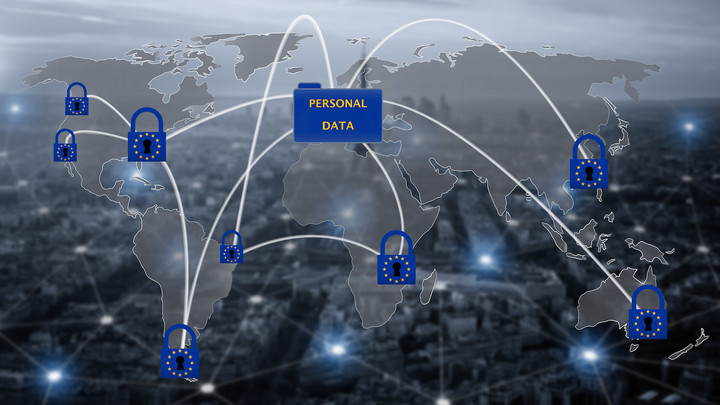
Is Your Data Safe? Exploring Security Concerns in Digital Transfers
In today's digital age, data transfers are an integral part of our daily activities, whether it's sending emails, making online purchases, or sharing files across platforms. However, with the increasing instances of cyberattacks and data breaches, it's crucial to ask: Is your data safe? One of the primary concerns during these digital transactions is the vulnerability of sensitive information. Cybercriminals utilize sophisticated methods to intercept data, making it essential for individuals and businesses to implement robust security measures. Adopting encryption, utilizing secure connections, and practicing good cybersecurity hygiene can go a long way in safeguarding your valuable data during transfers.
Furthermore, the type of digital transfer method you choose can significantly impact your data's safety. For example, File Transfer Protocols (FTP) often lack adequate encryption compared to more secure alternatives like SFTP or HTTPS. It’s also worth considering the platforms that handle your data; ensuring they are reputable and adhere to data protection regulations is vital. Always look for guidelines like the General Data Protection Regulation (GDPR) which emphasizes personal data privacy. As we explore these security concerns, remember that being proactive and informed is your best defense against the threats to your data vulnerability in digital transfers.